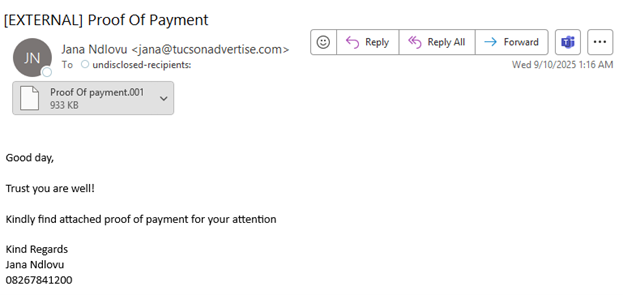
 The NJCCIC observed a malware campaign sent to New Jersey State employees, purporting to be proof of payment. The malicious emails contain a ZIP file labeled “Proof Of payment.001” with a SHA-256 hash. The ZIP file appears legitimate but includes a Microsoft EXE file labeled “u1ugeglmfc8xvoc” that drops several files, including a PowerShell script.
The NJCCIC observed a malware campaign sent to New Jersey State employees, purporting to be proof of payment. The malicious emails contain a ZIP file labeled “Proof Of payment.001” with a SHA-256 hash. The ZIP file appears legitimate but includes a Microsoft EXE file labeled “u1ugeglmfc8xvoc” that drops several files, including a PowerShell script.
According to VirusTotal, the malware likely belongs to the Krypt or Kryptik Trojan family. Besides malicious email attachments, Trojan infections can also occur by downloading and executing files from untrusted and unsafe websites. They can perform malicious activities on infected systems without the target’s knowledge, such as creating backdoors, establishing remote connections with command and control (C2) servers, maintaining persistence, and dropping other malware. Some can also target and capture keyboard input, such as account credentials, financial information, and other sensitive data.
In a similar campaign, researchers discovered phishing emails using malicious RAR attachments labeled “Proof of Payment.” If clicked, it launches the included VBE file using wscript[.]exe and drops several files, including a PowerShell script and a JPG file embedded with the DarkCloud stealer. If executed, DarkCloud uses process injection, outbound connections to suspicious top-level domains (TLDs), persistence, and data exfiltration. DarkCloud is programmed to steal account credentials from email and FTP clients and data from web browsers. The researchers observed an uptick in DarkCloud stealers targeting financial organizations in August 2025. These recent malware campaigns highlight the importance of awareness and strengthening defenses to help prevent threat actors from infecting systems and exfiltrating data to commit identity theft and financial fraud.
Recommendations
Refrain from responding to unsolicited communications, opening attachments, or clicking links from unknown senders.
Exercise caution with communications from known senders.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Download software or files only from reputable sources or websites.
- Use strong, unique passwords for all accounts and enable multi-factor authentication (MFA) where available, choosing authentication apps or hardware tokens over SMS text-based codes.
- Keep systems up to date and apply patches after appropriate testing.
- Run updated and reputable anti-virus or anti-malware programs.
- Report malicious cyber activity to the NJCCIC and the FBI’s IC3.
Reported from the NJCCIC Newsletter September 18, 2025


