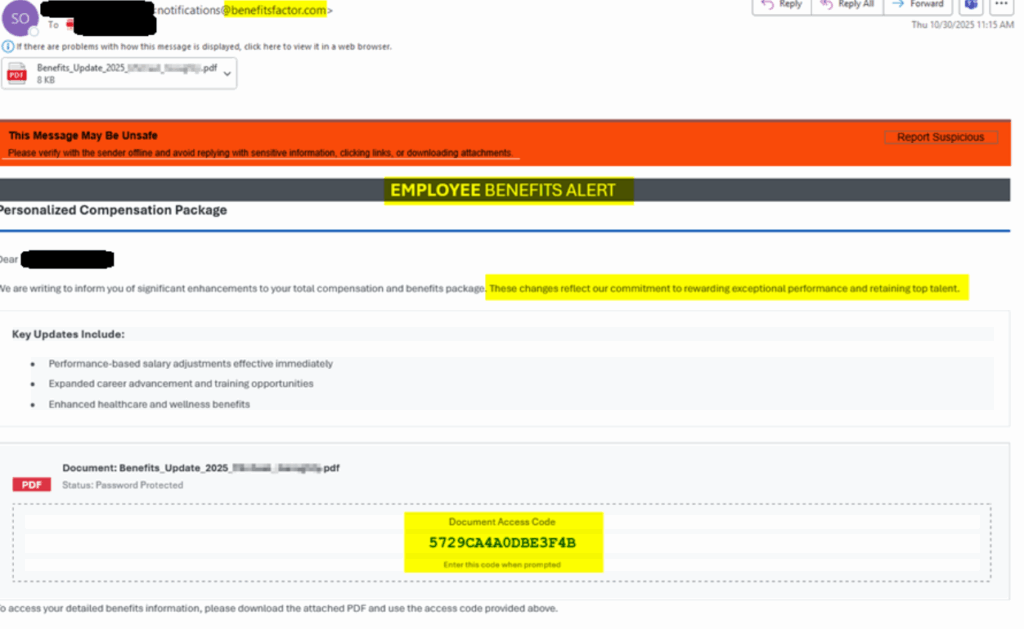
The NJCCIC observed a phishing campaign targeting several public sector organizations in New Jersey. These emails are sent from accounts ending in the domain “benefitsfactor[.]com” and contain subject lines similar to “Confidential: Compensation Update for (recipient).”
The body of the email references a benefits compensation package with an access code to open the attached document named “Benefits_Update_2025_(recipient).”
If opened, the document contains a link to access a secure portal. If clicked, the link directs the user to a webpage where they are asked to complete a security verification.
The user is then redirected to another webpage where they are prompted to log in with their Microsoft credentials in order to open the document.
The username is prepopulated with the user’s email address in an attempt to appear authentic. If the user submits their account credentials, they are stolen by the cyber threat actor behind this campaign.
 Recommendations:
Recommendations:
- Be skeptical of and exercise caution with any requests for personal or financial information, links to unexpected documents or messages, and urgent requests.
- If you are uncertain about the legitimacy of a message, contact the organization or individual mentioned in the message directly through official sources to verify the information and request.
- Avoid submitting account credentials to webpages unaffiliated with your online account.
- If you suspect an account has been compromised, notify your organization’s IT or IT security departments, change the account’s password immediately, enable multi-factor authentication, delete any inbox rules that have been put in place, and revoke any active sessions.
Report malicious activity to the NJCCIC and the FBI’s IC3 . Please do not hesitate to contact the NJCCIC at njccic@cyber.nj.gov with any questions. Also, for more background on our recent cybersecurity efforts, please visit cyber.nj.gov.


