The NJCCIC has recently identified a campaign using Adversary-in-the-Middle (AiTM) techniques to harvest user credentials for account compromise. Threat actors behind this campaign employ various lures to persuade targets to open the supplied file or click the provided link. Some messages claim to be a final document to review or a proposal based on a recent conversation, while others claim to be a link for a pending voicemail.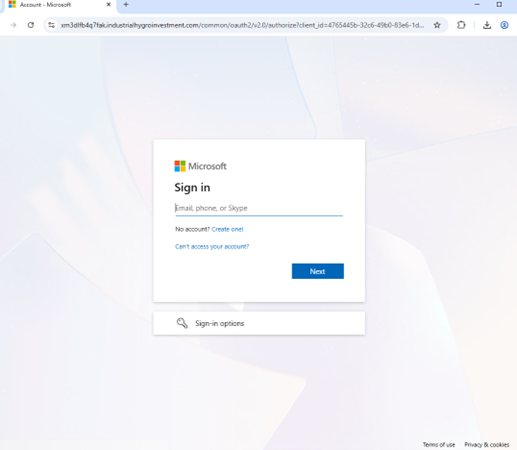
Following the PDF or link will lead users to a proxied Microsoft login page. After entering an email address, the webpage will display the organization’s Azure Active Directory (AAD) branding. Credentials, along with 2FA tokens and session cookies, will be captured in real-time through the Evilginx framework, which was originally designed to be a legitimate software tool for stress-testing a company’s security against phishing attacks.
Recommendations
- Avoid clicking links and opening attachments in unsolicited emails.
- Confirm requests from senders via contact information obtained from verified and official sources.
- Users should only submit account credentials on official websites.
- Maintain robust and up-to-date endpoint detection tools on every endpoint.
- Consider leveraging behavior-based detection tools rather than signature-based tools.
If you suspect an account has been compromised, change the account’s password immediately and add a secondary authentication method.
Report malicious cyber activity to the NJCCIC and the FBI’s IC3.
Orginally reported in the NJCCIC Newsletter Dec. 4, 2025